A Virtual Private Network (VPN) is a connection method used to add security and privacy and gives you the freedom to access the internet safely and securely from your laptop, tablet or smartphone when connected to an untrusted network, such as WiFi Hotspots in a hotel or coffee shop. Using a VPN connection you can circumvent geographical restrictions and/or censorship, and shield your location. When combined with an SSL certificate your connection will help to secure your wireless logins and communications.
When it comes to selecting a VPN, you have two choices; self-hosted using a VPS or from a VPN provider such as ExpressVPN or NordVPN. The basic difference between them is with a VPN provider you have anonymity without total control but a self-hosted VPN enables you to have total control with anonymity.
The OpenVPN protocol has long been accepted as the industry standard for VPN services, however, there is a new protocol called Wireguard that is predicted to challenge that. Although Wireguard promises better encryption and faster transfer speeds than OpenVPN, it’s still too new and support is not as widespread at the moment. At this time, our preferred VPN protocol at this time is OpenVPN due to it being a fully-featured mature protocol, open-source and offering a wide range of configurations.
In this guide, we will show you how to set up and configure OpenVPN on a server running CentOS enabling you to protect your privacy and browse the web anonymously. Install the required OpenVPN client software for MacOSX, IOS, Windows and Android and create additional users in OpenVPN.
Note
You don’t need a hugely powerful server to run OpenVPN. It will happily run on a NAT VPS server with as little as 128MB of RAM and 10GB of disk space.
If you are looking for a NAT VPS (256MB) provider we would highly recommend either Inception Hosting where you can pick up three different locations in Holland, United Kingdom and USA for only €12 or MrVM where you can pick up five different locations in Bulgaria, Italy, Germany, France, Norway for only $15.
Prerequisites
Update
Before completing the OpenVPN installation, we highly recommend that you update your system it ensure all packages are using the latest version.
yum update -y
TUN/TAP Module
If your VPS server is running KVM virtualization then you can skip this step. If your server is running OpenVZ virtualization you will need to ensure the TUN/TAP module is enabled on your server as OpenVPN depends upon it. You can check if the module is enabled with the following command.
cat /dev/net/tun
If the output returns cat: /dev/net/tun: File descriptor in bad state this indicates that the TUN/TAP module is enabled and you can proceed to the next step. If you get any other output such as cat: /dev/ppp: No such device or address then TUN/TAP module is not enabled on your server and you will need to contact your provider.
Check IP Addresses
Now we will need to find your servers IP address and make a note as it will be required later in the guide. You can find your IPv4 address using the following command.
dig -4 TXT +short o-o.myaddr.l.google.com @ns1.google.com | awk -F'"' '{ print $2}'Note
If the dig command is not found on CentOS, you will need to install the bind-utils package using the following command yum install -y bind-utils.
If your server also has IPv6 enabled you can find the address using the following command.
dig -6 TXT +short o-o.myaddr.l.google.com @ns1.google.com | awk -F'"' '{ print $2}'[root@vpsb ~]# dig -4 TXT +short o-o.myaddr.l.google.com @ns1.google.com | awk -F'"' '{ print $2}'
193.187.180.70
[root@vpsb ~]# dig -6 TXT +short o-o.myaddr.l.google.com @ns1.google.com | awk -F'"' '{ print $2}'
2001:7e05:3f11:cad3::bf65Install OpenVPN Server
Now that we have updated the system packages and made a note of the IPv4 address and if applicable the IPv6 address, we now need to install OpenVPN. To install OpenVPN we will be using the installation script from developer angristan which is available on GitHub as it is fully maintained and regularly updated. Prior to installing you can browse the scripts source code if needed. Although this guide is based on CentOS the script installer is designed to work with Debian, Ubuntu, Fedora and Arch Linux.
We will download the script directly from GitHub using the following curl command.
curl -O https://raw.githubusercontent.com/Angristan/openvpn-install/master/openvpn-install.sh
If you don’t have curl installed on your server or prefer to use wget, you can use the following command instead.
wget -O https://raw.githubusercontent.com/Angristan/openvpn-install/master/openvpn-install.sh
With the installation script downloaded, we now need to set up the required permissions to make the file executable. We change the permissions using the following chmod command.
chmod +x openvpn-install.sh
Now we will need to install the script using the following command.
./openvpn-install.sh
The installation script will ask you for your IPv4 address that you noted earlier and if you want to enable IPv6 support within OpenVPN. If you are not using a NAT VPS you will need to enable IPv6 support (NAT), otherwise you can select No. If you want to change the default listening port used for OpenVPN you can select option 2 or use option 3 for the script to choose a random listening port. Now you will need to choose the DNS resolver used OpenVPN, we would recommend that you choose a provider that offers worldwide anycast support such as Cloudflare or Google. For the next two options – compression and customise encryption settings – we would recommend you choose No. Then just press any key to continue.
[root@vpsbasics ~]# ./openvpn-install.sh Welcome to OpenVPN-install! The git repository is available at: https://github.com/angristan/openvpn-install I need to ask you a few questions before starting the setup. You can leave the default options and just press enter if you are ok with them. I need to know the IPv4 address of the network interface you want OpenVPN listening to. Unless your server is behind NAT, it should be your public IPv4 address. IP address: 193.187.180.70 Checking for IPv6 connectivity... Your host appears to have IPv6 connectivity. Do you want to enable IPv6 support (NAT)? [y/n]: n What port do you want OpenVPN to listen to? 1) Default: 1194 2) Custom 3) Random [49152-65535] Port choice [1-3]: 1 What protocol do you want OpenVPN to use? UDP is faster. Unless it is not available, you shouldn't use TCP. 1) UDP 2) TCP Protocol [1-2]: 1 What DNS resolvers do you want to use with the VPN? 1) Current system resolvers (from /etc/resolv.conf) 2) Self-hosted DNS Resolver (Unbound) 3) Cloudflare (Anycast: worldwide) 4) Quad9 (Anycast: worldwide) 5) Quad9 uncensored (Anycast: worldwide) 6) FDN (France) 7) DNS.WATCH (Germany) 8) OpenDNS (Anycast: worldwide) 9) Google (Anycast: worldwide) 10) Yandex Basic (Russia) 11) AdGuard DNS (Anycast: worldwide) 12) NextDNS (Anycast: worldwide) 13) Custom DNS [1-12]: 3 Do you want to use compression? It is not recommended since the VORACLE attack make use of it. Enable compression? [y/n]: n Do you want to customize encryption settings? Unless you know what you're doing, you should stick with the default parameters provided by the script. Note that whatever you choose, all the choices presented in the script are safe. (Unlike OpenVPN's defaults) See https://github.com/angristan/openvpn-install#security-and-encryption to learn more. Customize encryption settings? [y/n]: n Okay, that was all I needed. We are ready to setup your OpenVPN server now. You will be able to generate a client at the end of the installation. Press any key to continue...
Once the installation has completed, you will need to set up a new user configuration profile to use OpenVPN. Firstly, you will need to choose a client name but it must be only one word and contain no special characters. Many will choose client name related to the system the OpenVPN profile will be used on, for example, desktop for desktop VPN client or IOS for Apple iPhone. Then you will need to choose whether to protect the OpenVPN configuration file with a password, we would highly recommend that you encrypt the private key with a password for added security. This will means that whenever you start a VPN session, you’ll be required to add a password before the connection will be made. Once the VPN profile has been add the script will show the location of the configuration file.
Tell me a name for the client. Use one word only, no special characters. Client name: vpsbasics Do you want to protect the configuration file with a password? (e.g. encrypt the private key with a password) 1) Add a passwordless client 2) Use a password for the client Select an option [1-2]: 2 ⚠️ You will be asked for the client password below ⚠️ Note: using Easy-RSA configuration from: ./vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 Generating an EC private key writing new private key to '/etc/openvpn/easy-rsa/pki/private/vpsbasics.key.Cz6FtyqCXt' Enter PEM pass phrase: [YOUR_PASSWORD] Verifying - Enter PEM pass phrase: [YOUR_PASSWORD] ----- Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'vpsbasics' Certificate is to be certified until Apr 1 09:59:56 2023 GMT (1080 days) Write out database with 1 new entries Data Base Updated Client vpsbasics added, the configuration file is available at /root/vpsbasics.ovpn. Download the .ovpn file and import it in your OpenVPN client.
That’s it. You have now successfully installed OpenVPN on your CentOS server using the installation script from developer angristan. Next we will show you how to download the OpenVPN configuration file and install an OpenVPN client to connect to your VPN server.
Install OpenVPN Client
Now that the OpenVPN server has been successfully installed, we will need to download the OpenVPN client profile and then install OpenVPN client software on your computer, tablet or phone to connect to the OpenVPN server.
OpenVPN Client Profile
During the installation we created a new user configuration profile called vpsbasics.ovpn and is located in the root directory on the server /root/vpsbasics.ovpn. We need to download the .ovpn file to our computer so we can add it to the OpenVPN Client Software later. Depending upon your preferred method of transferring files, you can download the .ovpn file using an FTP client such as FileZilla or you can use Secure Copy Protocol (SCP) command.
To use SCP transfer method you will need to use the following command. Please note, that SCP will use the default SSH port 22.
scp user@remote_server:/remote/path/FILENAME /local/path/FILENAME
If you have changed the default SSH port on your server you will need to specify the port using the following command.
scp -P 1234 user@remote_server:/remote/path/FILENAME /local/path/FILENAME
OpenVPN Client Software
Now you will need to download the software to connect to the OpenVPN server.
- Apple iOS – Download the official OpenVPN Connect for iPhones and iPads from the App Store.
- Android – Download the official OpenVPN Connect for Android based phones and tablets from the Google Play Store.
- Apple macOS -Download Tunnelblick for macOS from their website.
- Windows -Download the OpenVPN community app from OpenVPN.
Once you have downloaded and installed the OpenVPN Client Software you will need to install the previously downloaded .ovpn file.
Test Internet Connectivity
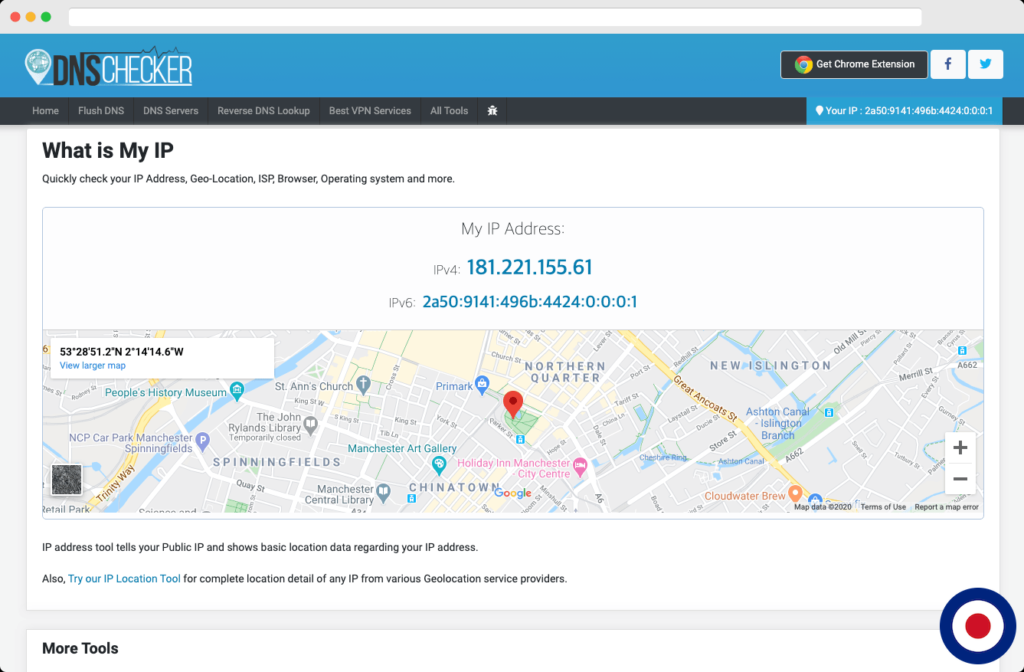
Now you need to test the OpenVPN server to ensure you can connected to the internet without issues. You can check access to the internet by visiting DNSChecker whilst connected your OpenVPN server. If everything is running as it should your servers IPv4 or IPv6 address will show up below My IP Address.
That’s it. You have now successfully installed the OpenVPN Client Software, installed a new Client Profile and tested your OpenVPN server to ensure it can connect to the internet. Next we will show you how to manage OpenVPN profiles by adding or removing users.
Manage OpenVPN Profiles
There may come a time when you want to add or remove users from your OpenVPN server. Luckily the process is extremely simple using the same script we used to install OpenVPN
Add OpenVPN Profile
You can add a new user OpenVPN configuration file using the following command.
./openvpn-install.sh
Once the OpenVPN installation script has loaded, simply select option 1 to add a new user and then choose the client name and add your required password option. Then download the profile using either FTP or SCP transfer methods and install to your OpenVPN Client Software.
[root@vpsbasics ~]# ./openvpn-install.sh Welcome to OpenVPN-install! The git repository is available at: https://github.com/angristan/openvpn-install It looks like OpenVPN is already installed. What do you want to do? 1) Add a new user 2) Revoke existing user 3) Remove OpenVPN 4) Exit Select an option [1-4]: 1 Tell me a name for the client. Use one word only, no special characters. Client name: vpsbasics Do you want to protect the configuration file with a password? (e.g. encrypt the private key with a password) 1) Add a passwordless client 2) Use a password for the client Select an option [1-2]: 2 ⚠️ You will be asked for the client password below ⚠️ Note: using Easy-RSA configuration from: ./vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 Generating an EC private key writing new private key to '/etc/openvpn/easy-rsa/pki/private/vpsbasics.key.ocsUr05JxD' Enter PEM pass phrase: Verifying - Enter PEM pass phrase: ----- Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'vpsbasics' Certificate is to be certified until Apr 1 10:05:30 2023 GMT (1080 days) Write out database with 1 new entries Data Base Updated Client vpsbasics added, the configuration file is available at /root/vpsbasics.ovpn. Download the .ovpn file and import it in your OpenVPN client.
Remove OpenVPN Profile
You can remove an existing user’s OpenVPN configuration file using the following command.
./openvpn-install.sh
Once the OpenVPN installation script has loaded, simply select option 2 to remove an existing new user and then choose the client name you want to delete.
[root@vpsbasics ~]# ./openvpn-install.sh
Welcome to OpenVPN-install!
The git repository is available at: https://github.com/angristan/openvpn-install
It looks like OpenVPN is already installed.
What do you want to do?
1) Add a new user
2) Revoke existing user
3) Remove OpenVPN
4) Exit
Select an option [1-4]: 2
Select the existing client certificate you want to revoke
1) vpsbasics
Select one client [1-2]: 1
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
Revoking Certificate EC369B2BAAC21A58946210BF7F9994D1.
Data Base Updated
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
An updated CRL has been created.
CRL file: /etc/openvpn/easy-rsa/pki/crl.pem
Certificate for client vpsbasics revoked.That’s it. You have now successfully set up an OpenVPN server on CentOS and installed the necessary OpenVPN Client Software, added a new Client Profile and fully tested its connectivity. You have also learnt how to add or remove user Client Profiles from your OpenVPN server.